Yang Luo A passionate generalist
I. Research & Engineering Projects
2. VisualPSD
Back
Jul 2012 - Dec 2012
BUAA, Key Laboratory of Beijing Network Technology
Project Description: VisualPSD aims to capture the packets received by the current machine and analyze whether there's malicious code mixed in them. The hackers usually utilize the delicately contructed packet to send to the vulnerable machines and the code the malicious packet is going to execute is called shellcode. So if we detect the shellcode contained in a packet, we are able to protect the host from the network attacks no matter whether the host is vulnerable or not.
Responsibility: I am responsible for all the design and programming work of VisualPSD.
Introduction: VisualPSD stands for VISUAL Packet Shellcode Detection system. Its main purpose is to capture the packets received by the current machine and analyze whether there's malicious code mixed in them. The hackers usually utilize the delicately contructed packet to send to the vulnerable machines and the code the malicious packet is going to execute is called shellcode. So if we detect the shellcode contained in a packet, we are able to protect the host from the network attacks no matter whether the host is vulnerable or not. VisualPSD uses WinPcap to capture the packets received by the host and BeaEngine to disassemble the packet bytes. Then we proposed a static and dynamic mixed approach for shellcode detection. For details see our paper, it's have been submitted to a EI journal.
Languages used by VisualPSD are:
C/C++
Techniques used by VisualPSD are:
MFC for UI
BCGControlBar for UI
WinPcap for packet capturing
BeaEngine for disassembling
Usage:
1) Install WinPcap before using VisualPSD.
2) Copy VisualPSD.exe from the "Debug" directory to the "dlls" directory, then execute it.
3) Click the "List NICs" button to list all the adpaters in the "Output" window, remember the "NIC WinPcap Index" is the ID of an adapter.
4) Fill in the "Source NIC" edit box with the ID of adapter which you want to capture. If you also fill an ID in the "Destination NIC", the packets from Source NIC will be redirected to the Destination NIC after handling.
5) Clicking "Capture" will trigger the WinPcap to start capture packets. Then click "Stop" will stop the capturing and "Clear" will clear the information displayed in UI. If you click "Capture & Disassemble" button instead of "Capture", the disassemble function will also start besides the capture function. The disassembly code will be displayed in the client area of VisualPSD.
Useful links:
Download source from GitHub
https://github.com/hsluoyz/VisualPSD
BCGControlBar official website
http://www.bcgsoft.com
WinPcap official website
http://www.winpcap.org
BeaEngine official website
http://www.beaengine.org
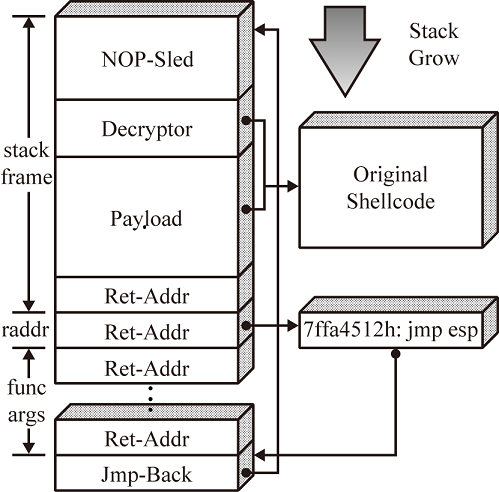
Fig.1. The structure of polymorphic shellcode.
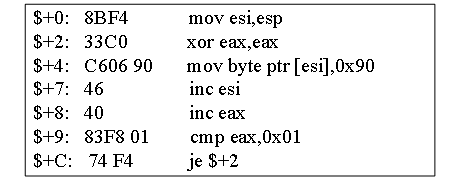
Fig.2. The Flush GetPC Method before flushing.
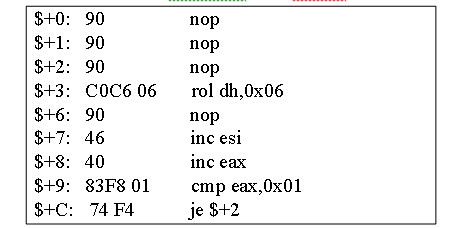
Fig.3. The Flush GetPC Method after flushing.
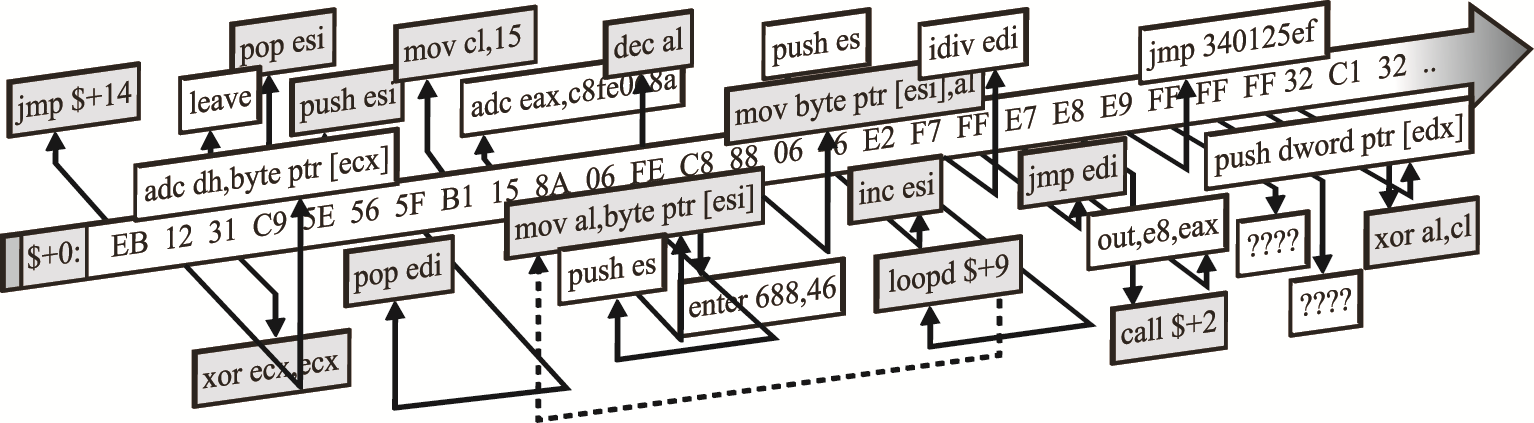
Fig.4. The Linux-x86 /bin/sh null-free polymorphic shellcode disassembled result.

Fig.5. The algorithm of calculating weighted pathes.
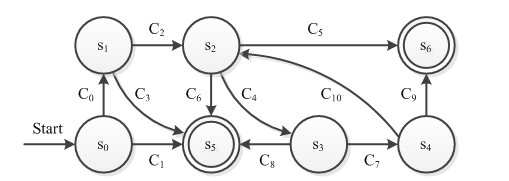
Fig.6. The Finite state machine of DVM method.
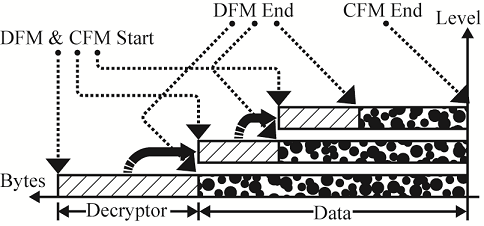
Fig.7. The structure of a 3-level polymorphic shellcode.
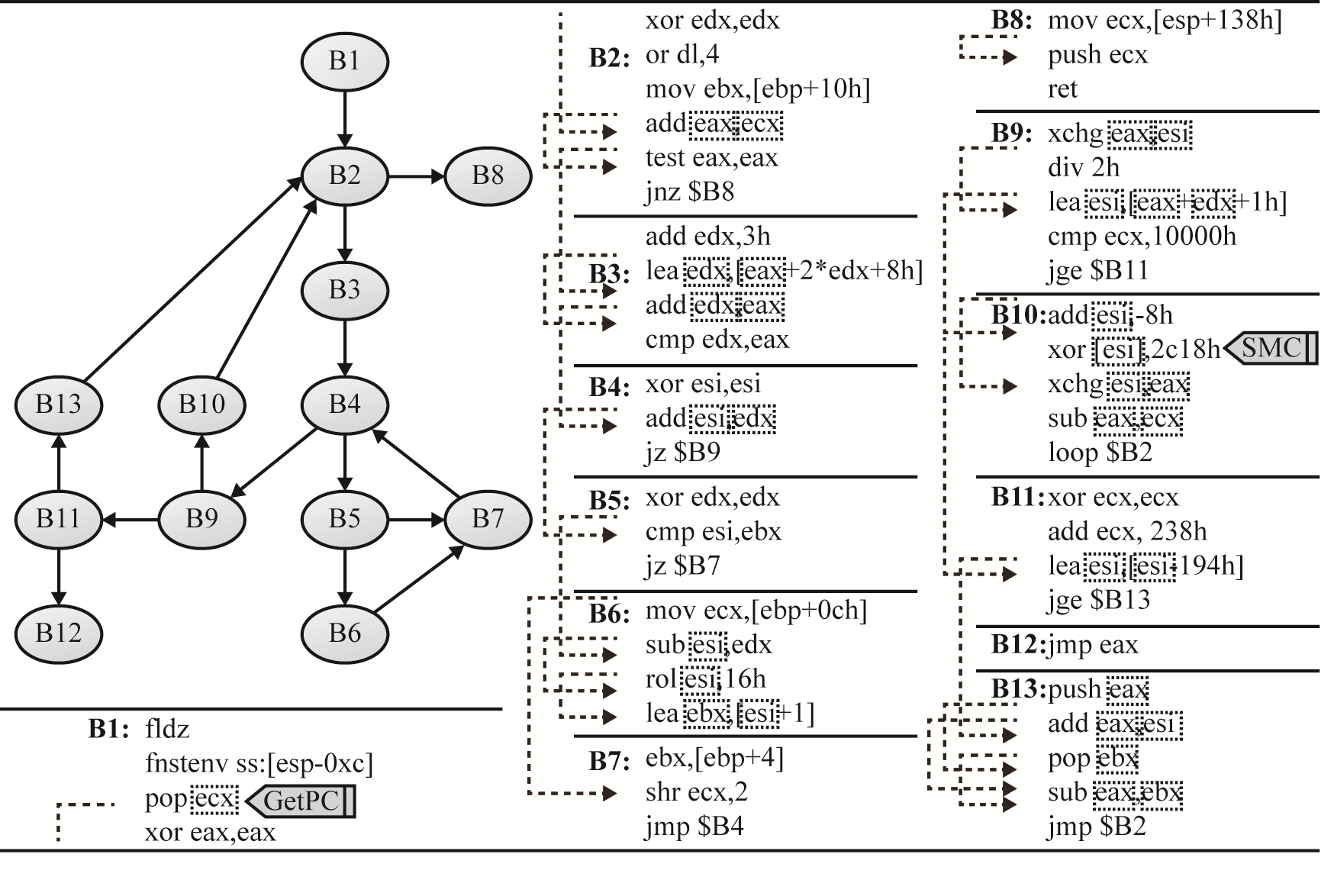
Fig.8. The Define-Use chains in basic blocks.
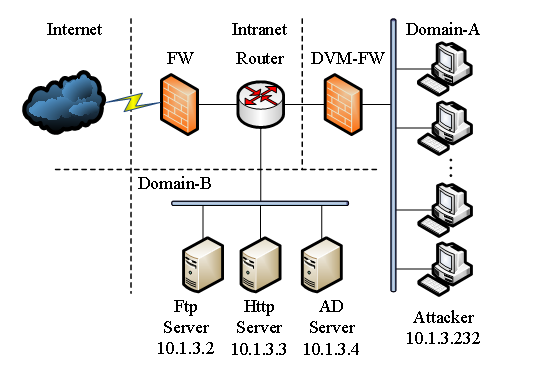
Fig.9. The simulation network for shellcode detection.
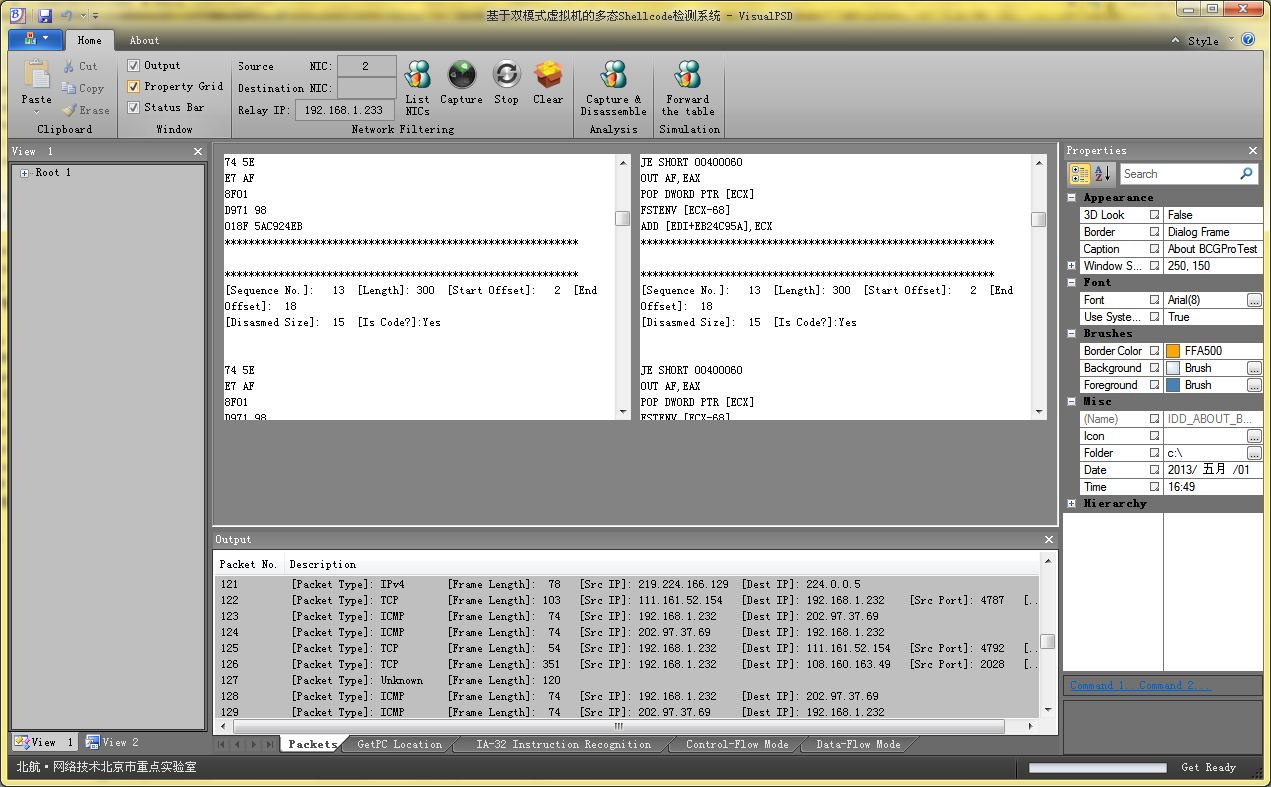
Fig.10. The main UI of VisualPSD.